2022. 3. 19. 03:31ㆍ0x0C Forensic/IR
Hello guys. Welcome to my IR practice room. Today, I solved one problem 'Insurance' located in incident-response-challenge.com.
Actually, you can get a flag easily. I had many questions about this challenge. Hence, I conducted a detailed analysis myself. While conducting the analysis, there was a lot of new knowledge and it was a good time to use the knowledge I had known before.
The person who offer the challenge did not know yet, but I had no choice but to admire the elaborate scenario that was written to create this challenge.
I really appreciate for providing a dump file to analysis this challenge.
This article was written according to the scenario I wanted to proceed in the event of an actual infringement accident. aka. Incident Response.
Well, I hope you enjoy reading it.
Noted. The article was quite long, so I summarised it in the overview, so if you do not have time, I think you can just refer to this also can.
If you have any queries, please feel free to contact me via reply.
If you have a good methodology to add, I sincerely welcome it.
Challenge: Insurance
Category: Forensic – Incident Response
Main Keyword: Lateral Movement
Author: Sangsoo Jeong
Client Information
| Claim Date | 04/02/2020 09:38 AM (UTC) |
| Customer | Robert |
| Requirement | Who changed my wallpaper? |
The investigator was handed overed one virtual disk from Robert. He tried to think about which methodology can change the client’s wallpaper. It was possible to predict the timeline range of infringement accidents from the disk name(‘2020-02-04T093816_PSexec.vhdx’).
The investigator confirmed the client’s windows version. The location is ‘C:\\Windows\\system32\\config\\SOFTWARE’. And, the data found on ‘Microsoft\WindowsNT\CurrentVersion’.
The time could convert via an Epoch Converter(https://www.epochconverter.com/).
| Name | Data |
| ProductName | Windows 10 Enterprise |
| Build | 15063.rs2_release.170317-1834 |
| Install Date | Monday, February 3, 2020 4:08:46 PM (UTC) |
[Table] Windows OS Information
Network Infrastructure
After research, the investigator made an infrastructure related to GOT.com.

[Figure] Network Infrastructure
Overview
1. The Active Domain of Robert’s company is related to LANNISTER.
2. The hacker used two servers. ‘STARK’ and ‘KINGS-LANDING’.
3. The hacker intended to hide an account. ‘STARK$’.
4. The shared directory setting for Robert’s company was insufficient.
5. The hacker inserted a network-related command(‘ipconfig’) to look into the AD environment.
6. The hacker used the PSEXECSVC application to make a lateral movement.
7. The hacker modified the wallpaper by modifying the registry value.
8. After changing the registry value, the hacker used the Rundll32 application to permanently save the registry.
9. The new user created by the hacker is GOT\varys-adm.
10. The attack’s internal IP are 172.168.18.156 and 172.168.18.154.
11. The Robert’s IP is 172.168.18.150.
12. Final attack uses MMC to remotely use an Anonymous account.
13. Run the gkape application remotely.
Base Information
According to the explorer, this disk has some information associated with the evidence.
The investigator mentioned the list below.
| No. | Contents |
| 1 | Log files |
| 2 | Partial of the C drive |
[Table] Discovered data related to the root directory
This computer has some credentials via a ‘C:\\Windows\\system32\\config\\SAM’. He enumerated the accounts table below. Additionally, he discovered a hidden account while he was during the analysis.
| Administrator |
| DefaultAccount |
| Guest |
| JonSnow |
| Tywin |
[Table] Discovered these data via a SAM
| IOC |
| KINGS-LANDING |
| STARK |
[Table] The table is shown IOC
Accessibility
Before proceeding with the analysis, he wrote the following scenario. Let’s look at the scenario below.
1. Remote Access
a. Phishing
b. SMB
c. Malicious code(Zombie PC)
d. RDP
2. Physical Access
a. Unlock the computer
b. USB
Attack scenario based in Remote Environment
Surprisingly, the ‘Robert’ account has not existed when investigator checked via a SAM. Luckily, the investigator discovered the account name ‘Robert’ into the disk at ‘C:\\Users\\%USERNAME\\’.
The wallpaper’s information was located at ‘Control Panel\\Desktop\\WallPaper’ on the ntuser.dat.
According to the research, only ‘Robert’ account has changed the wallpaper. It meant that the anonymous hacker succeeds to control his computer. By the way, the path is Share Folder(‘kings-landing’).
The investigator tried to find which the location ‘kings-landing’. And then, he decided the research flow which the attack scenario is related to Remote, not physical.
| User | HKCU Path | Contents |
| robert | C:\\Users\\robert\\ntuser.dat | \\kings-landing\share\lifeisur.jpeg |
| Default | C:\\Users\\Default\\ntuser.dat | C:\\Windows\\Web\\WallPaper\\Windows \\img0.jpg |
| JonSnow | C:\\Users\\JonSnow\\ntuser.dat | C:\\Windows\\Web\\WallPaper\\Windows \\img0.jpg |
| Tywin | C:\\Users\\Tywin\\ntuser.dat | C:\\Windows\\Web\\WallPaper\\Windows \\img0.jpg |
| varys-adm | C:\\Users\\varys-admin\\ntuser.dat | C:\\Windows\\Web\\WallPaper\\Windows \\img0.jpg |
[Table] The wallpaper was different only Robert.
This picture shows the Robert’s wallpaper information was modified by a malicious user.

[Figure] The picture is shown wallpaper information which the account is Robert.
In contrast, the user, JonSnow account still applied the default path about the wallpaper.
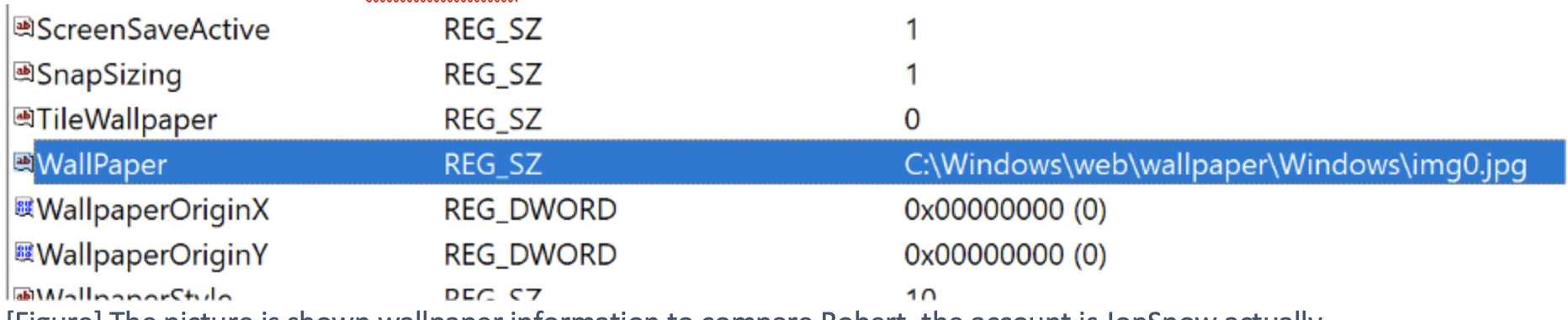
[Figure] The picture is shown wallpaper information to compare Robert, the account is JonSnow actually.
Investigator reminded the user ‘Robert’ made a dump file on 04/02/2020, 09:38:16 AM(UTC). In other words, the attacker can be possibly activated by 9 AM (UTC). And then, the investigator enumerated the suspicious process via a table based on after 9 AM. As well as the investigator recognized the computer region is Israel (UTC+2).

[Figure] The system timezone is Lsrael Standard Time
Investigator wrote the timeline based on the GMT table below.
| Name | Created Time (UTC) (04/02/2020) | Last Run Time (UTC) (04/02/2020) | Count |
| IPCONFIG | 9:01:07 AM | 9:01:07 AM | 1 |
| CMD | 9:01:05 AM | 9:16:54 AM 9:16:54 AM 9:13:39 AM 9:01:05 AM |
4 |
| PSEXECSVC | 9:13:01 AM | 9:13:38 AM 9:13:00 AM |
2 |
| REG | 9:14:02 AM | 9:15:11 AM 9:14:02 AM |
2 |
| RUNDLL32.EXE-3E9053B4 | 9:14:16 AM | 9:15:43 AM 9:14:16 AM |
2 |
| RUNDLL32.EXE-4F776BDC | 9:15:37 AM | 9:15:37 AM | 1 |
| MMC.EXE | 9:21:30 AM | 9:21:20 AM | 1 |
| GKAPE.EXE | 9:32:50 AM | 9:32:46 AM | 1 |
[Table] Suspicious behaviour was collected by prefetch.
It should be noted that after PSEXEC was executed, the Registry was dependent and executed, and RUNDLL32 was executed as a child process while changing a specific value of the Registry. The PSEXEC application can manage remote access. And then, this application must require administrator permission. It meant the Robert account was already linked the group of administrators. Because the investigator did not discover the behaviour which the attacker tried to bypass UAC. As well as the system already set UAC. More importantly, the hacker if use this application, he can access whenever he wants. This is a scenario that can occur in an APT attack. Currently, access to the internal network is successful, so it is impossible to imagine what attacks will continue in the future.

[Figure] Shown UAC is enabled
Additionally, the investigator realised why the user can be attacked. The wallpaper’s jpg file located on shared folder. The investigator discovered one misconfiguration relevant to the share folder. So, the computer can affect by the Null Session.
If ‘restrictAnonymous’ value is 0. This meant allowing access to the shared network from the outside.
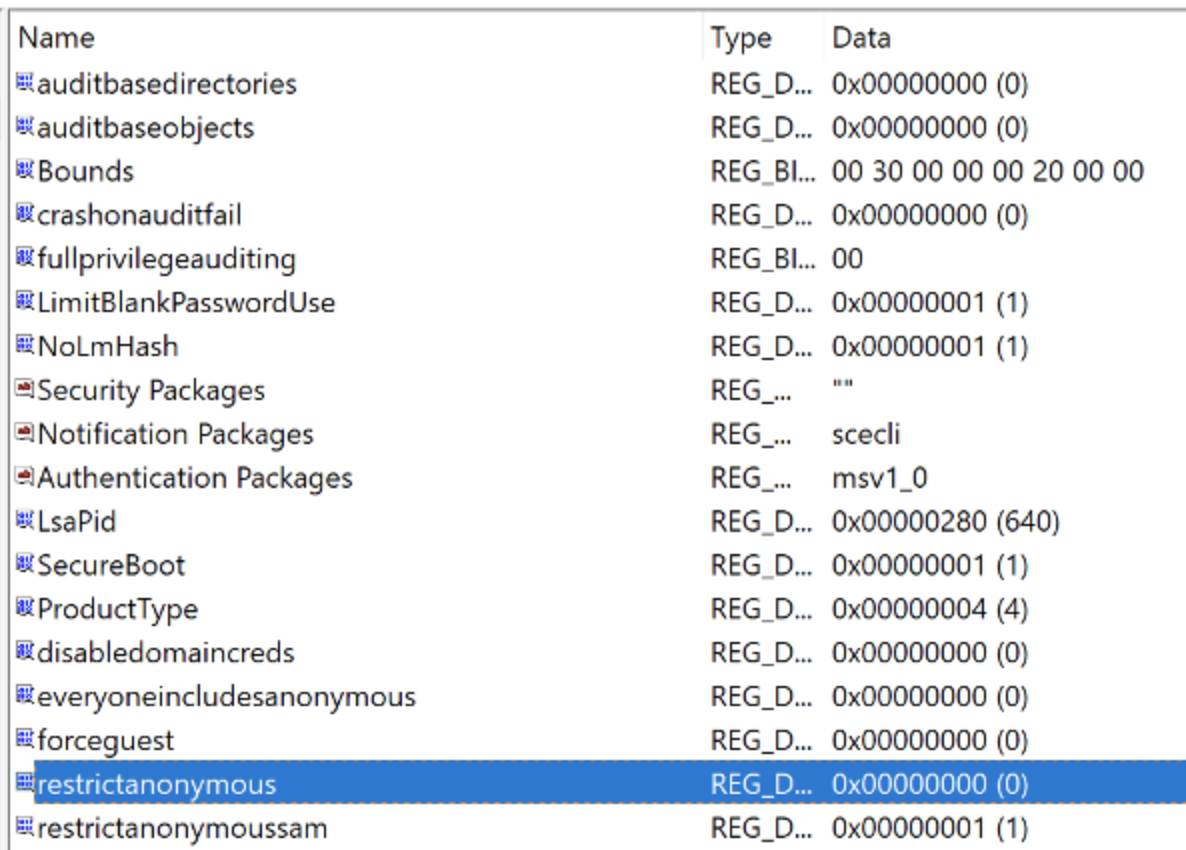
[Figure] Shared network is enabled
The following attack routes will be completed by redesigning based on the timeline. However, the investigator still has not discovered how hacker can upload the binary ‘PSEXECSVC’ on this client yet. Hence, when he was making a design the upload routine was just skipped.
After creating a remote account by running MMC, it was found that one program was running remotely.

[Figure] Redesignation of scenario referred to the timeline

[Figure] Redesignation of scenario referred to the timeline #2
How the attacker available this network area?
First, the investigator searched the keyword ‘SMBDeviceEnabled’ on the registry. Fortunately, this system did not have this value. Hence, the attacker could not use SMB to attack.

[Figure] Flag ‘SMBDeviceEnabled’ did not exist on the system
Investigator discovered that the NtpClient was only worked to manage time synchronisation. Therefore, the attacker did not attack by DOS as well. And then, found the keyword is ‘Kings-Landing’, This domain already revealed on Robert’s wallpaper absolute path. In conclusion, the ‘Kings-Landing’ is Active Directory. The investigator assumed the AD directory was hacked. So, the attacker can control several networks internally.

[Figure] C:\\Windows\\system32\\eventewt\\logs\\system.evtx
Analysis of Login credential – Logon Failed
The system does not have any credential related to logon failed. It meant the hacker did not try to use login via a RDP or SSH.

[Figure] The system log did not have an information about the ‘Logon Failed’
Analysis of Login/Logoff credential – Logon
The investigator was observed logon log standard on 4th February 2020, 9:15 AM.
To help you understand the table, share the Logon type of the Windows OS.
· 2: Login via a console
· 3: Login via a remote
· 5: Service
· 9: New credential
· 11: Automatically
I highly emphasis this information is important on this document.
Robert’s desktop IP is 172.16.18.150. (SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nia\Cache\InternetAuth OR SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces)
| Subject UserName |
Target UserName |
Computer | Process | IP | Logon type |
Time | Authentication PackageName |
| Before Threat | |||||||
| DESKTOP- HUB666E$ |
SYSTEM | DESKTOP-HUB666E | services | X | Negotiate | ||
| DESKTOP- HUB666E$ |
UMFD-0 | DESKTOP-H71RETA | winlogon | X | Negotiate | ||
| DESKTOP- HUB666E$ |
SYSTEM | DESKTOP-H71RETA [changed] |
services | X | Negotiate | ||
| DESKTOP- HUB666E$ |
DWN-1 (Windows Manager) |
DESKTOP-H71RETA |
winlogon | X | Negotiate | ||
| N/A | ANONYMOUS LOGON |
DESKTOP-H71RETA |
X | X | NTLM | ||
| DESKTOP- HUB666E$ |
defaultuser0 | DESKTOP-H71RETA | msoobe.exe | X | Negotiate | ||
| defaultuser0 | Tywin | DESKTOP-H71RETA | CloudExperience HostBroker |
X | Negotiate | ||
| DESKTOP- HUB666E$ |
DWN-2 |
DESKTOP-H71RETA | winlogon | X | Negotiate | ||
| DESKTOP- HUB666E$ |
Tywin | DESKTOP-H71RETA | svchost | 127.0.0.1 | 03/02/2020 16:16:16 |
Negotiate | |
| LANNISTER$ | SYSTEM | Lannister.GOT.com | services | X | Negotiate | ||
| LANNISTER$ | NETWORK SERVICE |
Lannister.GOT.com | services | X | Negotiate | ||
| LANNISTER$ | Admin | Lannister.GOT.com | |||||
| Date of occurrence of an incident | |||||||
| LANNISTER$ | Robert | Lannister.GOT.com | svchost | 127.0.0.1 | 2 | 04/02/2020 08:38:37 |
Negotiate |
| LANNISTER$ | admin | Lannister.GOT.com | consent | ::1 [IPV6] |
2 | 04/02/2020 09:05:14 |
Negotiate |
| admin | Logoff | 04/02/2020 09:05:14 |
|||||
| LANNISTER$ | varys-adm | Lannister.GOT.com | consent | ::1 [IPV6] |
11 |
04/02/2020 09:05:53 0106560Z |
Negotiate |
| LANNISTER$ | varys-adm | Lannister.GOT.com | consent | ::1 [IPV6] |
2 | 04/02/2020 09:05:53 0106812Z |
Negotiate |
| LANNISTER$ | varys-adm | Lannister.GOT.com | consent | ::1 [IPV6] |
2 | 04/02/2020 09:05:53 0106812Z |
Negotiate |
| varys-admin account creation time: 2020-02-04 09:05:53 7714148Z | |||||||
| N/A | Stanis | Lannister.GOT.com | 172.16.18.156:60292 | 3 | 04/02/2020 09:09:24 |
Kerberos | |
| N/A | Stanis | Lannister.GOT.com | 172.16.18.156:60294 | 3 | 04/02/2020 09:09:24 |
Kerberos | |
| N/A | Robert | Lannister.GOT.com [Workstation] : X |
172.16.18.156:60299 | 3 | 04/02/2020 09:09:41 |
Kerberos | |
| Robert | Logoff | ||||||
| N/A | Robert | Lannister.GOT.com | 172.16.18.156:60306 | 3 |
04/02/2020 09:12:39 |
Kerberos | |
| N/A | STARK$ | Lannister.GOT.com [Workstation]: X |
172.16.18.156:60306 | 3 | 04/02/2020 09:12:40 |
Kerberos | |
| Logoff | |||||||
| N.A | STARK$ | Lannister.GOT.com | 172.16.18.156:60306 | 3 | 04/02/2020 09:12:41 |
Kerberos | |
| PSEXESVC first Runtime: 02/04/2020 09:13:00 | |||||||
| N/A | Robert | Lannister.GOT.com | 172.16.18.156:60306 | 3 | 04/02/2020 09:13:17 |
Kerberos | |
| PSEXESVC second Runtime: 02/04/2020 09:13:38 | |||||||
| LANNISTER$ | robert | Lannister.GOT.com [Workstation] : LANNISTER |
PSEXESVC | X | 2 | 04/02/2020 09:13:39 1812991Z |
Negotiate |
| Logoff | |||||||
| LANNISTER$ | robert | Lannister.GOT.com [Workstation] : LANNISTER |
PSEXESVC | X | 2 | 04/02/2020 09:13:39 1813089Z |
Negotiate |
| After configuration about the MMC –> Create ‘ANONYMOUS LOGON’ to access remotely | |||||||
| N/A | ANONYMOUS LOGON | Lannister.GOT.com [Workstation]: STARK |
X | 172.16.18.156:60338 | 3 | 04/02/2020 09:21:45 |
NTLM |
| LANNISTER$ | SYSTEM | Lannister.GOT.com [Workstation]: X |
5 | ||||
| X | ANONYMOUS LOGON | Lannister.GOT.com [Workstation]: KINGS-LANDING [LogonProcessName]: NtLmSsp [Key len]: 128 |
X | 172.16.18.154:64551 | 3 | 04/02/2020 09:31:24 |
NTLM |
| Execution GKAPE.exe | |||||||
| X | ANONYMOUS LOGON | Lannister.GOT.com [Workstation]: STARK [LogonProcessName]: NtLmSsp [Key len]: 128 |
X | 172.168.18.156:60345 | 3 | 04/02/2020 09:33:49 |
NTLM |
[Table] Logon processes discovered before PSEXESVC was executed
The above table shown some information about the incident response.
The GOV\varys-adm user was created on 4th February 2020, 09:05 AM.

[Figure] Varys-adm creation time
Through the varys-adm ntuser.dat, it was confirmed that the time when the registry key was last modified and the time when the user was created matched. It can be seen that the first generation of the registry is also considered a modification.

[Figure] The picture shown varys-adm’s ntuser.dat
The following ntuser.dat value (Desktop\\Wallpaper) proves that Rundll32 and svchost are deeply related to Desktop Window Manager(DWM).
| Process Name | Time |
| REG.exe | 09:15:14 |
| SVCHOST.exe | 09:15:37 |
| Desktop Window Manager(DWM) | 09:16:30 |
| Change registry key |
[Table] Information about the process and time related to wallpaper’s behaviour
Netlogon
Netlogon failed to retrieve the password for got\robert at +1 second location when PSEXEC.exe was executed. However, the ‘log on failed log’ did not reveal it at System Evtx.

[Figure] Execute PSEXEC(5:13:38, 5:13:00)
Conclusion
Due to restricted files (windows event, prefetch, registry), it was not known whether the PSEXEC program was deleted after the attack or whether the program was on the hard disk continuously when the client generated the dump file.
In the case of PSEXESVC, it was located at 172.16.18.156, and the probability of switching wallpapers by entering robert’s account and remote command is low possibility.
The PSEXESVC handled by Robert(‘S-1-5-21-1466640861-467201727-801756312-2604’) and Logon Type was set 2. The Investigator double-checked via a System log, 7045 event ID.

[Figure] Compared WinPrefetchView and System log file(Event no. 7045)
In order to check the operation process of the PSEXESVC application, event numbers 7045(installed), 5145(create another process/file share), 4697(account), and 13(changed EULA key) of the Winevt System can be filtered and inspected. In the current system(‘Robert’), only the result value of 7045 was derived.
It may be an externally initiated hacking, but according to the log, it was possible to infer only limitedly that the attack began on the internal network.
Even if, it was confirmed that the SMB and RDP were limited, it was also confirmed that the hacker used the client account (‘Robert’) in a remote environment via MMC application.
The client needs to identify who the team member is using IP(‘172.16.18.156’).
GOT corporation seems to need to further strengthen its access to shared directories.
During log file analysis, it is revealed that the “STARK$” account was also suspicious. In windows, if the username is included ‘$’, this account can use as a hidden account.
Unfortunately, since it was accessed remotely, in-depth analysis was not performed in the current system.
Although PSEXESVC’s role has changed only the wallpaper through registry modification, it is recommended that PSEXESVC be blacklist filtered out if it is using EDR system form GOT because hackers can launch secondary attacks seems like persistence.
According to the research, After PSEXESVC, the hacker create new account via a MMC and upload another application to proceed with the attack from his C2 server(‘KINGS-LANDING’). Therefore, caution is required because continuous attacks may occur when the report is being written seems like persistence.
In other words, by changing the wallpaper, the attacker will be able to start the attack as a reminder, and Robert’s quick judgement will reduce further damage on his system. However, once again, it is necessary to look at the behaviour after uploading the GKAPE application.
Reference
https://jpcertcc.github.io/ToolAnalysisResultSheet/details/PsExec.htm#Findings
'0x0C Forensic > IR' 카테고리의 다른 글
| [Challenge] Find Frog - incident-response-challenge.com (0) | 2022.03.24 |
|---|---|
| DB (0) | 2022.03.16 |
| Hello Dok (0) | 2022.03.16 |