2020. 1. 26. 04:23ㆍ0x0C Forensic/rootme
Goal : Find Hostname
Category : Memory Analysis
Description
You have requested a memory dump but before starting your analysis you wanted to take a look at the antivirus’ logs. Unfortunately, you forgot to write down the workstation’s hostname. But since you have its memory dump you should be able to get it back!
Almost Forensic File is so big data.
This binary is 177MB (Compressed by tbz2).
For most memory analyses, a tool called volatility is used.
I discovered some profiles (relavated Win7).
This is Document of Volatility.

DLL List can't confirm hostname.

We recognize that this problem's goal is finding 'hostname'.
and Already offered hint. "antivirus’ logs"
So, i decided that not use 'volatility'.
I was tried hex application. and then, i found this word.
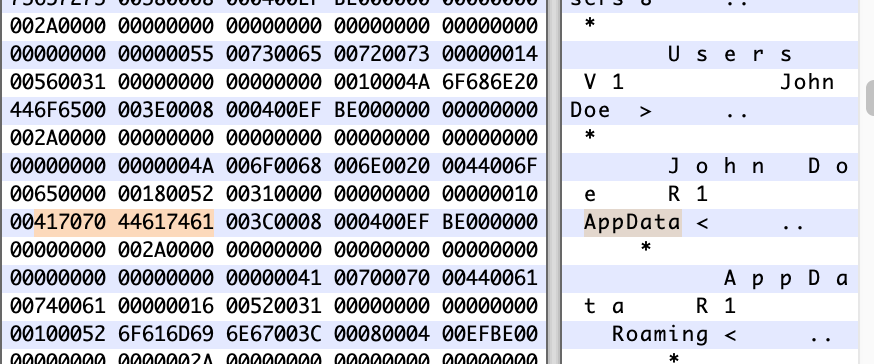
This Word is 'AppData'. It meant that contained all of Windows Operating System.
for example. C:\Users\c0nstant\AppData\ ..
That's why I thought that JohnDoe is hostname. Unfortunately, it is not flag.
Therefore, I recognized this is not workstation's name.
Soon, I thought abt another idea.
I discovered 'cmdline' among the volatility command option.
vol.py -f ./ch2.dmp --profile=Win7SP1x86_23418 cmdline
and.. I knew it was John Doe, not JohnDoe, and I realized that I missed '0x20' from Hex Data.

What?? It is not flag !! ..
Oh.. Suddenly I realized John Doe is Computer Name, not HostName.
I imagined how can i see HostName in Win OS.
First Trying : dumpregistry
I didn't find clue.

Second Trying : hivelist
vol.py -f ./ch2.dmp --profile=Win7SP1x86_23418 hivelist
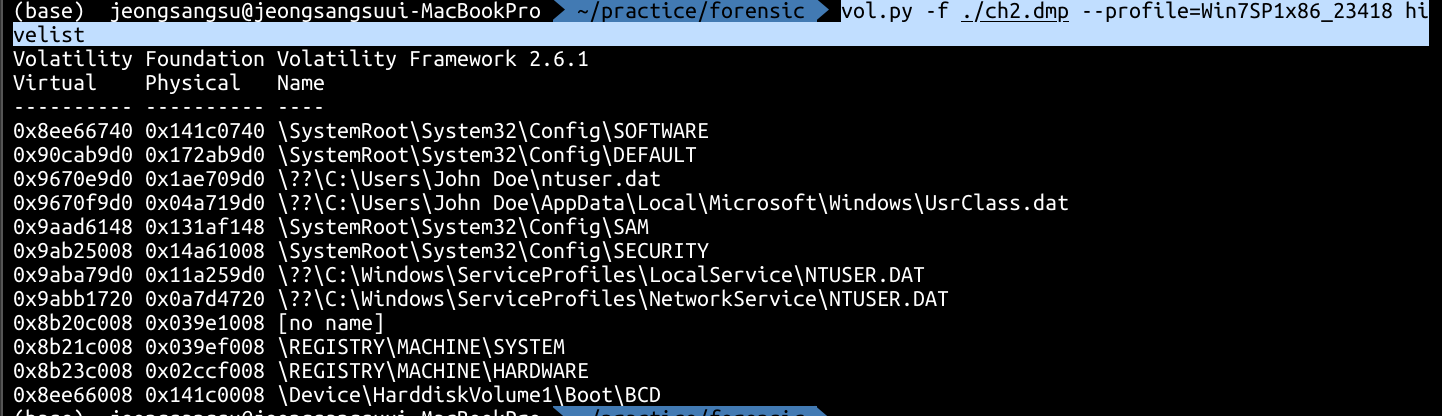
And then, I found this path through google.
Key word : where is hostname stored in registry

The google informed for me, "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\ComputerName"
and I already found "\REGISTRY\MACHINE\SYSTEM"
MACHINE == HKEY_LOCAL_MACHINE == HKLM
Finally, Several trials and errors, starting with the keywords in question, have finally gained the flag !!
key word : how to use registry context using volatility's plugin hivelist (didn't get any information)
First Try

Second Try

Third Try
How to find CurrentControlSet\Control\ComputerName\ComputerName using in Volatility's plugin hivelist
vol.py -f ./ch2.dmp --profile=Win7SP1x86_23418 printkey -K "controlset001\control\computername"
How to find HostName in "\REGISTRY\MACHINE\SYSTEM" using by Volatility
vol.py -f ./ch2.dmp --profile=Win7SP1x86_23418 printkey -o 0x8b21c008 -K "ControlSet001\Control\ComputerName\ComputerName"
Get A FLAG !!

